Used domain name is being targeted -What is the "DNS takeover" attack that is included in the DNS setting error
Event report
Internet Week 2020
On November 26, "Internet Week 2020" was held online online.This year's lecture title is "Thinking about the operation management of DNS in the Managed Service era -DNS takeover as a theme", and the speaker Yasuhiro Morishita and Nao Kojin of the Japanese registry service (JPRS).Taro said, "I would be grateful if you could enjoy each lunchtime while listening to DNS stories!"
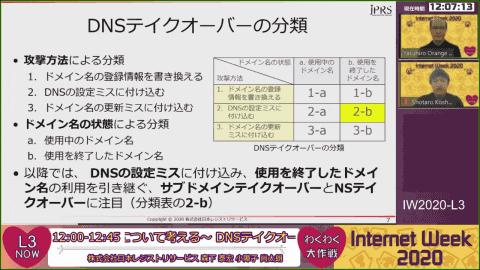
table of contents
▼ "DNS settings remaining" is an operation threat. ▼ Excessive expectations for DOH and DOT are prohibited.
"DNS settings that remain remaining" will be an operation threat
In recent years, attacks attached to DNS setting mistakes have been noticeable.There are various reasons for setting mistakes, but the spread of various services in DNS has also indicated that the person in charge of management and operation is the lack of knowledge of the person in charge of management and the service itself, which is a risk of operation.It is getting to be done.
At the beginning, Mr. Kojuko introduced the outline of "DNS takeover", which is the center of this topic in part 1 in the seminar.DNS takeover is an act of using the DNS mechanism to take over the use of domain names unintended (Fig. 1).It is a representative example of the use of the DNS that remains even after the use of the domain name is inherited in the "subdomain takeover" or "NS takesover" (Fig. 2).。
図1 DNSテイクオーバーとは?図2 DNSテイクオーバーの分類The difference between the attack method similar to the DNS takeover was introduced as follows.The difference between DNS takeover and "Domain name hijack" that readers know is that in the drop catch, it is used in the domain name update error (Fig. 3), and used in the domain name Hijack.It is often used in the nuance of depriving the domain name management authority (Fig. 4).
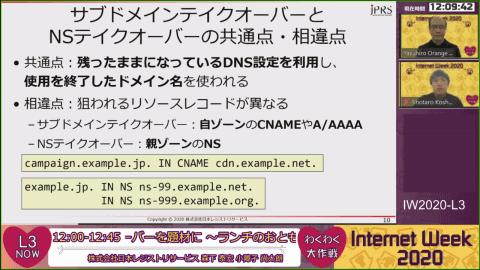
図3 DNSテイクオーバーとドロップキャッチの共通点・相違点図4 DNSテイクオーバーとドメイン名ハイジャックの共通点・相違点Sub -domain takeover is attached to the fact that the CNAME resource record and A/AAAA resource record set at the start of use of external services are not deleted, and inherit the use of the sub domain using the settings.It is something to do (Fig. 5).For example, if there is a setting where the sub domain of the organization specifies the CDN server remains, if a third party can re -set the server with the same name to the CDN, the third party will succeed in taking over the subdomain.It will be.
図5 サブドメインテイクオーバーとは?NS takeover is included in the lame delegation, in which the name server information set in the registry is not deleted at the start of the use of external DNS services, that is, the domain using the settings.It is to take over the use of the name (Fig. 6).Similar to the subdomain takeover, if a third party can reset the authority DNS server in the same zone on the DNS service, the third party will also succeed in taking over the domain name.
図6 NSテイクオーバーとは?In this way, the common point of subdomain takes and NS takeover is that the administrator has forgotten the DNS settings to take over the domain name (Fig. 7).Such resource records that remain after use are called "Dangling Records" and are one of the threats in DNS operation (Fig. 8).
図7 サブドメインテイクオーバーとNSテイクオーバーの共通点・相違点図8 Dangling records