Started free provision of "am I infected?", A malware inspection service for IoT devices such as home routers.
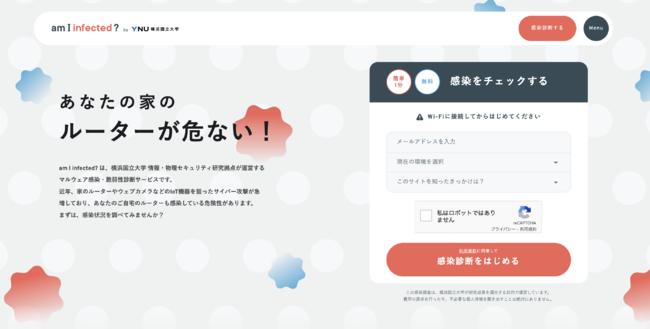
"Am I infected" top page
This service is a free service that allows users to inspect and take countermeasures by themselves whether IoT devices such as home routers and smart home appliances are infected with malware or used in a vulnerable state. The test results will be sent to the email address entered by the user within 5 minutes, and we will inform you about recommended measures in case of suspected malware infection or if the IoT device is in a vulnerable state. (* 1) Malware is an abbreviation for "malicious software" and is a general term for programs that cause infected devices to operate illegally and harmfully. ■ Background of service provision The Yokohama National University Information and Physical Security Research Center has been conducting research on security measures for IoT devices since 2015. Cyber attacks targeting IoT devices continue to increase (* 2), and in particular, with the spread of the new coronavirus infection, telework has become widespread as a new normal way of working, so home routers, webcams, etc. The importance of ensuring the security of IoT devices is increasing. Malware-infected IoT devices continue to operate unchanged after infection, so even if they are infected, it is difficult for users to notice. Therefore, we have started a service to inspect for malware infection and vulnerabilities with the aim of continuing to use IoT devices at home with peace of mind. (* 2) Ministry of Internal Affairs and Communications: "Recent trends in cyber attacks, observation of cyber attacks by NICT (NICTER)" URL: https://www.soumu.go.jp/main_content/000771974.pdf ■ Overview of this service This service Is a free service that allows users to easily inspect whether IoT devices such as home routers and smart home appliances are infected with malware or are still vulnerable. From the dedicated site (https://amii.ynu.codes/), enter the e-mail address to send the test results and answer the questionnaire about the environment where the test is performed, so that you can use it when you access the website. We will inspect your IP address. The test result will be sent to the email address you entered with a link to the test result page. In the unlikely event that you are suspected of being infected with malware, you will take the measures yourself by referring to the recommended measures on the same page.
Display example of safe state
Display example when malware infection is suspected
The Information and Physical Security Research Center of Yokohama National University is conducting research to derive countermeasures based on actual observations and analyzes of cyber attacks. The decoy system "Honeypot" attracts cyber attacks, and passive observations that observe in detail and active observations that search for vulnerable systems that are the targets of attacks are used to grasp these situations and perform unique analysis. By clarifying the mechanism, effective countermeasures can be derived. We have observed and analyzed cyber attacks and malware infections in IoT, and ultra-large-scale denial of service attacks, and provided the observation and analysis results to a large number of public institutions, private companies, and research communities. Zero Zero One provides support for IoT device developers to eliminate security concerns at the design stage and prevent unexpected threats, as well as enlightenment activities to ensure safe and secure use of IoT devices. It is a company that does. It was created to eliminate the anxiety of an era when it became commonplace to connect to the Internet with the spread of IoT devices. Our main business is Karma, a search engine that visualizes various information including OSINT, and consulting services for safer product development.