Providing safe and secure to connected cars by stealth encryption and high -precision position control ── terrilogy - Wirelesswire News
At Tokyo Motor Show Symposium 2017, a symposium was held by the Secure IoT Platform Council, "Aiming to realize a safe and secure car society -thinking about the security of connected cars".At the symposium, terrilogy's executive fellow Shinmitsu -man, which provides the design and construction of network/security solutions to operation management, gave a lecture on safety and security measures, including the car itself and a factory that manufactures various products.
It is said that most of the new cars will be connected cars in 2020.By connecting the car sensor to the Internet, a number of new services that make use of driving data will be born.In addition, smooth automatic driving is possible by obtaining high -precision maps of real -time and road traffic information.
In these environments, comprehensive measures are required for threats such as unjust remote control and cyber attacks, overlooking society as a whole.In fact, Chrysler Jeep Cherokee found a vulnerability that the ECU (in -vehicle electronic control unit) could be hijacked by remotely, and 1.4 million units were recalled.In addition, the security measures for connected cars are a major issue for car manufacturers, including Kaspersky, an IT security company, publishing articles on Tesla Motors' electric model S on a blog.At this time, Tesla responds by automatic update.
Although it is not a car, there are cases of actual damage.In May 2017, the damage of the ransomware "Wannacry" spread around Europe.German railways could no longer display timetables, and Romanian automakers had severe damage, such as stopping production lines.
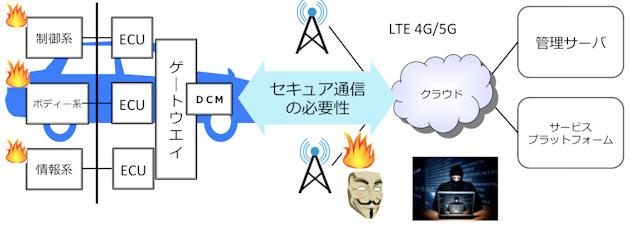
So what measures are possible to enhance the security of a connected car?And I want to look at the relationship with the security of the "connected factory".The keywords are "stealth encryption network", "high -precision position control", and "real -time acquisition and management of information".
Stealth a car from the hacker so that it cannot be seen
The first stealth encryption network is to secure communication using a network that does not see end devices from outside when interacting with vehicle control data between a vehicle and a service center.It is called "stealth encryption network" because the target is invisible.
This is a technology used as a security solution to protect the "connected factory".Using the next -generation secure communication protocol HIP (Host Identity Protocol) technology, a method of making the device into stealth mode and invisible from the outside is adopted.It is a technology represented by Tempered Networks HIP switches.HIP is a secure communication protocol that is standardized in IETF, which can be used by using a unique encryption ID by using HIP instead of conventional IP (Internet Protocol).
Various important infrastructure around the world uses the SCADA (SUPERVISORY CONTROL AND DATA ACQUISITION) system that remotely intensively monitor production systems, which is the target of attackers.However, using a stealth network, hackers cannot find the end device and secure security.By using this technology, connected cars will not be able to find hackers.
Other IoT platform services include HIP software on IoT gateway and HIP switches to IoT platforms such as data centers, so that LPWAN (Low Power Wide Area Network) and mobile communication network are overlayed.It is possible to cover the end device.
Control autonomous cars with high -precision location information
The second is a solution that increases the accuracy of location information for the vehicle control of an autonomous car.A service that provides accurate vehicle position by combining the actual GNSS measurement value of the measured engine (GNSS: Global Navigation Satellite System, satellite positioning system) and the Internet correction value.
For example, if you combine the Freewave technology in the United States with the Swift Navigation technology, you can achieve high -precision positioning of automatic driving cars.FREEWAVE's Freewave Radios is a RTK-GPS for autonomous driving (Real Time Cinematic GPS) sends correction information from a familiar point to a mobile phone or wireless, and sends the location of the mobile station in real time.It can be measured.Swift Navigation has developed advanced modular positioning systems designed for autonomous driving, and the company's Starling Navigation Engine engine software combines the actual GNSS measurement value of the hardware measurement engine and the correction value of the Internet.Vehicle location information can be obtained accurately.
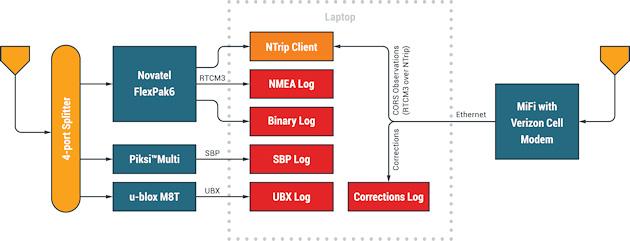
Swift Navigation has demonstrated a demonstration verification of automatic driving in San Francisco, demonstrating that it can reduce the number of centimeters of positioning, which was about 10m, to several centimeters.The Swift Navigation vehicle positioning system can provide necessary accuracy to realize the next -generation autonomous vehicle application that requires a lane or sablain -level position.The test hardware of this demonstration experiment consists of an active GNSS antenna connected to a 4 -port passive RF splitter that distributes GNSS signals to various GNSS receivers.Furthermore, it is connected to the Internet by connecting to a laptop PC (installed in the car) via an Ethernet cable using a Verizon USB cellular modem.
Source: HIGH-PRECISION GNSS Autonomous Driving Localization Test WHITE PAPER
Acquire and manage vehicle information in real time
Introducing solutions that acquire and manage vehicle information in real time as a third measure to enhance the security of connected cars.This is a self-failed diagnosis called OBD (ON-BOARD DIAGNOSTICS), a computer (ECU) mounted on a car.
Terrilogy's capital tie -up Nex offers the OBD II -type automobile telematics data collection unit "GX4X0NC".It corresponds to more than 1200 models in Japan, the largest in the industry, and can be installed on various special vehicles.Acquired driving data includes 10 basic data, such as instant fuel economy, vehicle speed, acceleration, and GPS location information, and up to 38 other vehicles depending on the model.
By combining multiple solutions like this, it is possible to create a secure system.Terrilogy wants to provide these technologies and solutions to support the construction of security and security in connected cars and "connected factories" to protect security and security.
