Serious development environment design utilizing OpenShift on IBM Cloud | Medium
In this article, IBM hosts on IBM Cloud "Redhat OpenShift on IBM Cloud" (hereinafter, OpenShift on IBM Cloud), a managed service for enterprise, "Serious development test in anticipation of long -term use.We will tell you about your worries, questions, and how to respond when configuring the environment.
The second story explains "worries at design: private network configuration" for intermediate and advanced users.
When selecting a development tool for container environments and starting designing a development test environment, the network configuration of a private development test environment is confusing.Even for intermediate and advanced people who have some knowledge of container environments, I would like to hold down the unique elements of Openshift on IBM Cloud.
In the construction of corporate systems, there are many cases where the development environment wants to be built in a private network of companies.
The reason is that there are related systems and development test environments in private networks such as data centers and corporate servers, and applications built on the cloud need to be linked to those systems, and are being developed and under development.They want to reduce the risk of accessing programs and test data as much as possible.
Some IBM Cloud public services are used only from private environments.
With experience architect, you can somehow imagine a network configuration on such a premise.
(1) IP addresses are private, (2) the environment in the cluster (development, test, staging) is separated in the name space, ③ Connect to the network in the company via VPN, (4) from the container to the IBM public service ((4) from the container.You may imagine that DB2 Warehouse, Watson API, etc. (such as Watson API, etc.) can be accessed only from private IP addresses, and the third -party services with only public IP addresses are connected with a secure protocol such as HTTPS.
However, if you actually try to design, you will notice that the public access services provided by the public cloud are mainly information on public access, and the information in the private structure is very limited.
From this, we will explain the following three questions about the private network configuration of the development test environment in OpenShift on IBM Cloud.
Question 1 How to connect to a cluster in a public cloud only with private IP. 2 How can the container be published to a private IP?
The first thing to worry about in the private network configuration in the development test environment is, "Is it a cluster in a public cloud, but can it be connected only with private IP?"
The answer is that "whether private access in public cloud is possible depending on the vendor and service provided by the managed service."
First, check if only private IP is connected for the service to be used.
In the case of IBM Cloud, it supports a private network configuration, but some services only support public network access.
In general, the latest information needs to be confirmed because the configuration of cloud services is constantly supported.For IBM Cloud, there are two types of private network configurations.
The first is the "Classic Infrastructure" that has existed since the old Softlayer era, and the second is the new architecture "virtual private cloud (VPC) infrastructure".
If you ask the name, it seems good to use the latter, but unfortunately at the time of writing (June 2020), version 4 which is the latest version of OpenShift on IBM Cloud..3 and version 3, which is the previous version.In 11, "virtual private cloud (VPC) infrastructure" is not supported (Red Hat OpenShift on IBM Cloud Service Restrictions-Version 4.3 Cluster restrictions).
Therefore, the use is "classic infrastructure".
Also OpenShift on IBM Cloud version 4.In 3, it is also important to note that private access (called "private service endpoints") to "master node" that manages the cluster is not supported.
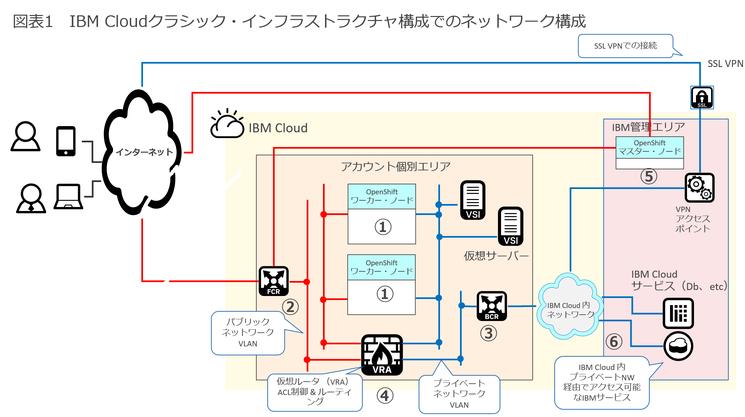
Figure 1 describes the key points of the private network configuration of Openshift on IBM Cloud using classic infrastructure.
(1) Worker nodes that operate the application can be connected to any virtual LAN (hereinafter referred to as VLAN), so it is necessary to specify one public VLAN and one private VLAN.
(2) The router that is the entrance to the public VLAN dedicated to each user account from the Internet is "FCR (Front-End Customer Router)".
(3) The router that is the entrance to the private VLAN exclusively for each user from the IBM Cloud Private Network is the BCR (BACK-END CUSTOMER ROUTER).
VRA (Virtual Router Appliance) is connected to private VLANs and public VLANs, and provide firewalls, traffic shaping, policy -based routes and VPN functions.FCR, BCR, and VRA are IBM Cloud -specific terms, but I want to remember it because it is indispensable for the IBM Cloud network configuration by classic infrastructure.
⑤ Openshift on IBM Cloud is a managed service, so the master node (also called a service endpoint) that manages the cluster is managed, which requires access on the public network side.
⑥ Managing the right to access the OpenShift cluster, IBM Cloud Identity and Access Management (IAM), and the IBM Cloud Container Registic IBM Cloud Container Registry required for arranging additional containers.It is necessary to secure.These are located inside IBM Cloud, but are not a user but an IBM management IP address space.
I think the basic structure has been suppressed so far.For a network configuration, in addition to these, it is necessary to understand the network configuration in OpenShift and Kubernetes containers.
The second question about the private network configuration in the development environment is "How to publish applications to private IPs."
If the container is performed according to the basic manual or tutorial, it will be published in the public IP, and there is little information about the release of the private IP.I would like to introduce what I understood as an example.
Access to the application on the OpenShift cluster is generally used with OpenShift's proprietary Router or a general -purpose Ingress of Kubernetes, and the OpenShift cluster runs the sorting process.
In the default cluster configuration, both Router and INGRESS are published in the public IP address, so it is necessary to first set up to publish Router to a private IP address.
OpenShift on IBM Cloud version 4.Let's explain the rough flow of the additional setup performed in 3.For detailed procedures, setting Up Basic Load Balancing with An NLB 1.See 0.
First, create an IngressController resource and create a new Router.
Next, create a Service resource for a new Router and publish Router to the Load Balancer of the private IP.As an option, edit the IngressController definition of the default Router published in the public IP and configure the private Route definition so that it is not published to the default Router.
You can configure a private Router so far, but to publish the application there, first of all, the OpenShift project (Kubernetes name space) is the Label of Route, according to the rules of the label selector specified in the Route settings.There is a method to set.
Furthermore, when creating Route, use the Hostname option to specify the host name to be resolved into the private IP address.
There is little information about private configurations, so I would like to tell you that this trend has actually achieved a private network configuration.
What should I do to access the development test environment a private network configuration and access the applications placed in that environment from the development terminal?
First, access to the application on OpenShift cluster is roughly divided into two.
The first is a method of using the Router (or Ingress) as described above to sort it based on the host name (virtual host name) and context route used during access, and this is basically http/https.Only is eligible.
The second is the Kubernetes Service to use the network road balancer service (NLB), and the method of assigning an IP address is targeted, and any TCP/IP service is eligible.It can also be used when accessing the database operated by a container on the cluster directly from outside the cluster.
Here, we will explain the method of assigning with a virtual host name using the first Router or INGRESS.
As an example, consider the case where two applications for the web and API are running in each name space in the integrated test environment and staging environment.
Containers in the integrated test environment are common virtual host names (example, App1-IT).MyDomain.Internal), and each application is accessed separately after the host name.
For example, the web container is/Web/, and the API container is "https: // app1-it.MyDomain.Access with Internal/API/.
The virtual host name of the staging environment is "App1-STAGING.MyDomain.Internal "is also divided by the path after the host name, and the web container in the integrated test environment is https: // app1-it..MyDomain.Internal/API, staging environment API containers are https: // app1-staging.MyDomain..Suppose you want to access with Internal/API/.
In order to achieve this, as shown in Figure 2, the development terminal is to resolve the IP address of the same Router for both the virtual host name of the IT environment and the staging environment, and the access destination Router is the terminal.It is necessary to sort out the access destination service (container) depending on the virtual host name and path accessed.
At this time, it is necessary to consider the name resolution from the development terminal to the Router.
Regarding the name resolution, if there is a DNS server for a company or public, how to register a domain for the development environment, how to configure DNS proxy software on the development terminal, and solve it into an IP address (IP address ().nip.There are methods to use IO, etc.).
For the sorting of the host name and path in Route, there are methods to explicitly specify the – Hostname option of the OC Expose command, and to specify Hostname in the Route resource definition.
For specific settings, refer to the manual of the product (Redhat OpenShift Container Platform 4).3-secured Routes).
So far, we have introduced three common questions when building a development test environment in a private network using Openshift on IBM Cloud.Actually, the private network configuration of the development environment has other additional needs and traps, so I would like to introduce it if there is another opportunity.
Japan Eye Bee M Systems Engineering Co., Ltd. Cloud Application Advisory IT Specialist
Since joining the company, he has been involved in the technical support of test automation solutions in various industries and systems, and has been in charge of the development test tool chain in container environments to the system construction.
[I Magazine 2020 Summer published]
・ ・ ・ ・ ・ ・ ・ ・ ・
Start from the base 1 foundation, an overview of OpenShift networks and uses for example Part2 OpenShift on IBM Cloud Serious development environment design _Selow for proposals: Selection of development tools for container environments _ Selections of second editions: Development Test TroubleEnvironmental private network configuration _ Trouble when operating the second part: Efficiently backup method in Part3 OpenShift using the OpenShift function to develop the development test environment efficiently
