
The misunderstanding of "backup = data protection"! What is the reason why Cyber Ricabry is now required?
Initatives such as DX (digital transformation) and work style reform are progressing, and the importance of data has never been more than ever.However, the consciousness of data protection is still strong, and it is still noticeable that it has led to business damage.For example, business suspension by ransomware attack.Meanwhile, Del Technologies Co., Ltd. pointed out that it is important to have a different data protection consciousness from the conventional backup for the New Normal era.We asked the company's person in charge of thinking and approaching data protection.
The impact of data rosts on business has become so big
Business digitalization has accelerated, and the dependence on corporate IT systems is rapidly increasing.Data is one of the most important factors that make up IT.The data handled by companies is accelerating, and the business process itself is composed of data, as well as the source for analysis.
For example, the workflow of the business process that connects cloud services.The IoT data and SNS data recorded in the cloud service are intended to be automated using RPA to link and analyze the core system in the API.In this case, everything is important and indispensable, such as non -structured data accumulated in the cloud, code for API linkage, structured data of core systems, and RPA configuration management information.
However, how to protect such data is still conspicuous.In the above example, there are many cases where the backup of the core system data and the configuration data has been backed up, and that has done it.The current situation is that it is important to be aware of the differences between backup and data protection, "said Toshiori Suzuki, director of DPS Business Division, DPS Business Division, DPS.
"The business impact when the data is lost due to system disorder or human mistakes is incomparable to the past. Backup is just one of the means of data protection. Not only is it just backed up.It is becoming more important to protect the data to continue. "(Mr. Suzuki)
Simply backup is not enough! Data protection awareness
One of the easy -to -understand cases in mind the "difference between backup and data protection" is the recent ransomware attack.Ransomware is a cyber attack that encrypts data and demands ransom for cancellation.When ransomware is damaged, it is extremely difficult to decrypt the encrypted data, and the only solution is to restore data from backup.
However, when it comes to advanced and clever ransomware, it has a mechanism that not only encrypts the local data of the PC, but also deletes backup data on the network in advance.For this reason, in the "simply backed -up" state, there is no way to regain the data.
"Advanced ransomware can disable the backup mechanism of Windows volume shadow copy service (VSS), or destroy backup data acquired to the NAS etc. with conventional backup software.There are many cases where data, including backup, has been lost, so that data protection is always in consideration of such risks, backing up into a completely isolated environment, and whether the backed up has been tampered with.It is important to check and manage things that can be restored properly from backup. "(Mr. Suzuki)
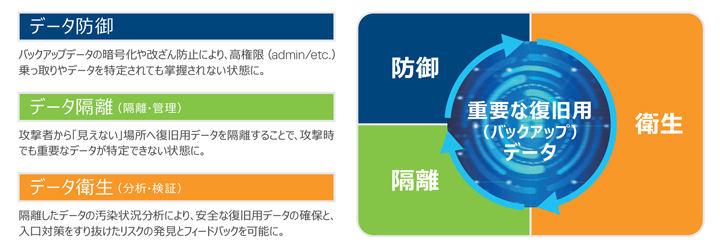
According to Suzuki, the important point of view is "fusion of backup and security."It is said that not only "copy and save data" is required as a backup to properly manage backup data along the security framework.
What is "network isolation" for reliably responding to ransomware attacks?
At that time, the CSF (Cyber Security Framework) of NIST (US Standard Technical Research Institute), one of the famous security frameworks, is a reference.NIST CSF recommends measures against cyber attacks for each phase of identify, defense, detection, correspondence (RESPOND), and recovery (recover)."When protecting backup data is to operate from the viewpoint of security measures," Suzuki emphasizes Suzuki.
However, in order to operate the backup mechanism along the cyber security framework, it is necessary to combine various tools and operate them integrated.It is easy for many companies to build and operate a new mechanism that combines security measures as the load on the person in charge alone is increasing due to the increase in the amount of data.Under such circumstances, Suzuki proposed "data network isolation" as "the first step".
"Network isolation is an approach that is isolated in a space blocked from an external network and properly manages recovery data so that it can be restored correctly. The basics of backup are stored in different media or different places.It is to do. For example, the tape backup used in mission critical systems, etc., records the safety of a different media called tape, and sends it to a different location, which is enhanced. The same mechanism is handled by today's company.It applies to all the data you are. "(Mr. Suzuki)
Cyber Recovery Solution is provided by Del Technologies as a solution that can easily realize network isolation and recovery data management of data.
"Cyber Recovery Solution" that realizes advanced data protection by extending backup
Cyber Recovery Solution is a solution to provide functions such as data defense, data isolation, data hygiene, etc. by utilizing the data protection appliance "Dell EMC PowerProtect DD/DP Series", and realizes the improvement of cyber resilience in companies.。Data defense is a function to prevent backup data encryption, falsification, or destruction by hijacking with high authority (such as ADMIN).Data isolation is a function that realizes network isolation and recovery data management described above.Data hygiene is a function to analyze isolated data and verify whether data recovery can be implemented without risk.
"If you use Dell Emc PowerProtect Cyber Recovery, you will be able to recover in an emergency on an extension of normal operation while utilizing existing backup operation. It is physically isolated using data isolation.By configuring the "air gap" network, ransomware, etc. prevents falsification and preserves recovery data. It is safe and reliable due to network isolation from the operation of saving backup copies in a shared folder on the NAS.Data protection can be built quickly "(Suzuki)
Even if a network separation (air gap) is a manual work like a remote storage of the tape backup, the operation load will increase.In addition, tape backup requires a lot of time to recover data, and it is difficult to analyze the data evacuated to the tape and check the hygiene condition, which involves the risk of restore.DELL EMC PowerProtect Cyber Recovery automates data link connections and connection settings for network isolation by policy control.In addition, recovery data is generated, and locks and defense to prevent tampering are automated by policy control.Furthermore, these can be set and operational management by dedicated UI and dashboard.
DELL EMC PowerProtect Cyber Recovery is the only solution provider, Sheltered Harbor.Non -profit organization Sherbed Harbor aims to protect US financial institutions, its customers, and financial systems from the serious damage of cyber attacks, and in 2015, the financial industry has become higher and increasing.In order to respond to, it is an initiative led by the industrial industry.
Providing appliance for mid -sized environments that can be used from 999 million yen
Various technology provided by PowerProtect also helps to strengthen data protection.The technology adopted by PowerProtect is a unique technology that is different from the conventional backup, and no attack that abuses Windows OS or middleware vulnerabilities.In addition, by utilizing the unique duplicate exclusion and compression technology, the data transfer amount can be reduced as much as possible.It is possible to quickly recover not only backup time, but also if the business stops due to ransomware attack.
"File servers are scattered at the base, mainly on the NAS, and it is difficult to manage, and the backup of PCs brought back on telework has not been able to get backup, and in recent years, it is likely to be damaged by cyber attacks along with changes in working style.However, it may be difficult to introduce a new security solution in terms of convenience and costs. At that time, it is an extension of the backup, the protection of data security and data.DELL EMC PowerProtect Cyber Recovery, which can respond to business continuity and RTO requirements, will help you greatly help "(Suzuki).
Along with the complex IT system, security solutions that need to be introduced are more complicated, and the operation management costs tend to increase.In particular, security solutions, which are difficult to read for mid -sized businesses, are often struggling to introduce them.Del Technologies has launched a "Cyber Rica Barry Package 999", a DELL EMC PowerProtect Cyber Recovery Startup Package, which provides only backup data isolation by air gap, to support such mid -sized businesses.I am (limited time campaign).
"In order to bring out value from data, it is not enough to just develop a" road "for data utilization. It is important to develop" guard rails "and" traffic lights "for safe proceeds. Organization.Please work on data protection for business growth "(Mr. Suzuki)
Dell EMC PowerProtect Cyber Recoveryのお問合せはこちらから>>>
[PR] Provided: Del Technologies
