Attack flow using “Frame Aggregation” that exploits A-MSDU
Attack flow using Frame Aggregation Virtually all IPv4/v6 client traffic can be intercepted
Up to the last time, we introduced three types of attack methods, and finally we conducted a demonstration test. Although only the results have been summarized, I would like to explain the story of the attack method in a little more detail.
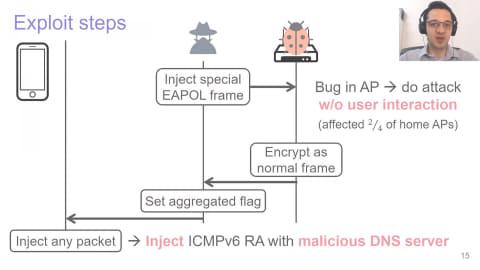
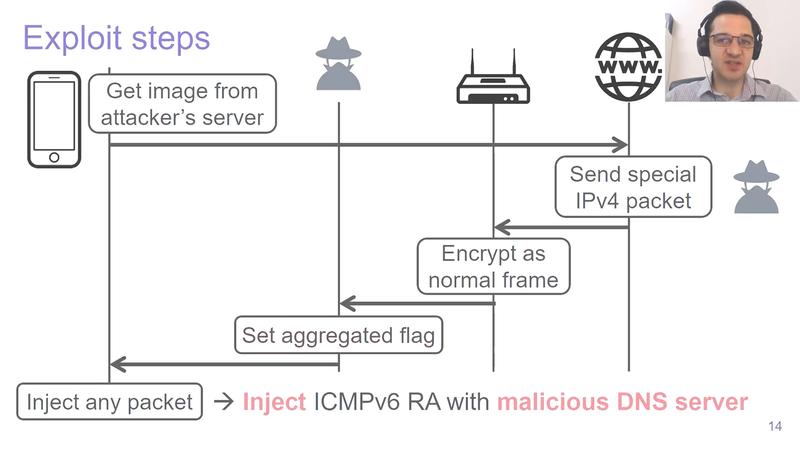
First, let's take a closer look at the first attack using Frame Aggregation, and the flow of the attack that appears in the diagram below.
Attack examples for clients (top) and access points (bottom). Source: "FragAttacks: Presentation at USENIX Security '21" (YouTube)First, for IPv4 and IPv6 hosts, port scan and open based on encrypted TCP SYN/ACK response length Detected port. On the other hand, an IPv4/v6 dual stack client can be injected with ICMPv6 router advertisements to trick the victim into using a DNS server under the attacker's control.
More precisely, it exploits IPv6 stateless address autoconfiguration to inject ICMPv6 router advertisements containing malicious DNS servers. It has been confirmed that this can "poison" the DNS server used by the OS on Windows 10, macOS 10.15.4, Linux, Android 8.1 and iOS 13.4.1.
In this method, once the victim uses the malicious DNS server installed by the attacker even once, the attacker can redirect all traffic to the malicious server under their control. All IP-based traffic can be intercepted.
By the way, above I said I hosted an IPv6-based malicious DNS server, but it is possible to have it respond to DNS requests with an IPv4 address if desired.
