
"intimidation diversity" that extends to blackmail software groups: the further evolution of double intimidation
The means and techniques of blackmailing software groups to force the payment of ransoms are no longer just threats to disclose data or sell to others. Peter Mackenzie, director of incident response at Sophos, said that as companies' data protection technology had improved, blackmail software groups began to supplement their requirements with new intimidation methods.
"using the stolen personal information to frighten the victim by texting employees by name or calling personally, they saw the means of demanding ransom from the employer."
"such methods indicate a change in Ransom software from purely technical attacks targeting systems and data to attacks targeting humans." (McKinsey)
iStock.com/style-photographyData theft and disclosure are the most frequently used means. If you are attacked by blackmail software, it is appropriate to consider that you may have been violated by data first. A survey conducted by Sophos showed that data including the results of traffic accident investigations, such as drivers' names and deaths, were stolen in Conti attacks against transport and logistics companies.
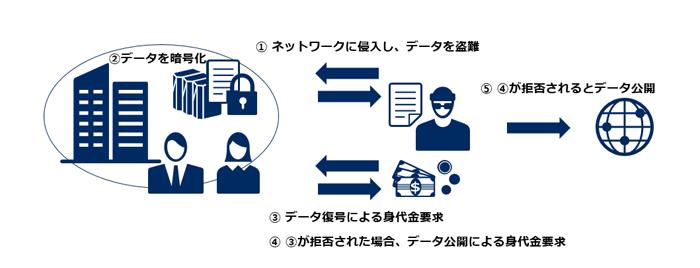
The second most common is the aforementioned means of intimidating "disclosure of personal information" by e-mail or phone calls. This is often used by Conti, Maze, REvil, and SunCrypt.
The third method used is related to the second. This is a means of reaching out to individuals and businesses related to the information owned by the victim and threatening to persuade the victim to pay the ransom. This is mostly used by Cl0p and REvil.
The fourth is the means to warn the authorities not to report and silence the victims. Recently, the means of warning the media not to tell the media have also increased. The original purpose was to prevent victims from turning to others for help in order to avoid paying ransom. It is said that recently there is a tendency that Lanson Software Group will care about its own image.]
In October 2021, Conti expressed dissatisfaction with the disclosure of the negotiation process with JVC Kenwood and commented that if the negotiation process fell into the hands of the media and researchers, it would stop the negotiations and stubbornly disclose the data obtained.
The recent rapid spread has been to recruit internal stakeholders of the target in exchange for a reduction in ransom and to attack extortion software on others. In the case investigated by Sophos, criminals who manipulated "LockBit 2.0" advertised along with ransom demands to recruit people to participate in attacks on third parties and partners of the victimized business.
There are other ways to hinder the victims'IT activities in some way, spark new unease and increase the likelihood of paying ransoms. Reset the password of the domain name administrator so that he cannot log in, delete all backups, launch a DDoS (distributed denial of service) attack on the target website, print ransom memos continuously, and make the office printer unavailable.
"even if files are encrypted, they can be recovered from backups, so attacks are no longer limited to encryption. This shows how important the multi-layer defense approach is. "(McKinsey)
